Does Research Using Social Media Platforms Require Research Ethics Board Review?
Guidance in Applying TCPS 2 (2022)
Table of Contents
Part I: Context
Part II: Guidance
- Does research using SM platforms require REB review?
- General ethical considerations and questions related to research using SM platforms
Part III: Practical Application
- Scenarios
- Scenario 1: Collecting information from closed forums
- Scenario 2: Research using information in the public domain
- Scenario 3: Research involving public figures
- Scenario 4: Researcher with connection to participants
- Scenario 5: Research involving data linkage
- Scenario 6: Participatory research with potential for identifiability in dissemination
Part I: Context
1. Introduction
The use of social media (SM) platforms provides new avenues and extended opportunities for researchers to access information created by SM users, to expand the scope and breadth of the pool of prospective participants globally, to understand and assess human behaviour in new contexts, and to facilitate collecting information from sources that may otherwise have been difficult to access. However, the use of SM platforms for the purpose of collecting research data also raises some ethical issues, questions, and considerations that apply to its context, and may involve varying levels of risk.
Researchers may apply different or mixed methods and methodologies when using SM platforms to collect data or to recruit participants in their research. They may directly interact with prospective participants, for example, by asking them to respond to surveys or to perform certain tasks. Researchers may also use digital information stored on SM platforms without direct interaction with human participants, for example, by means of harvesting, scraping (a technique where a computer program extracts data from human-readable output coming from another program), observing, or recording existing information stored on SM platforms. They may also observe patterns and behaviours of SM users in real-time, such as their reactions to a live stream.
The Tri-Agency Panel on Research Ethics (PRE) offers this guidance to further support research ethics boards (REBs) and researchers in the ethics review process and the ethical conduct of research that involves using information that exists on, or has been collected via SM platforms (referred to throughout this document as using SM platforms). The guidance is intended to support the community's educational initiatives and context specific considerations in the application of the Tri-Council Policy Statement: Ethical Conduct for Research Involving Humans – TCPS 2 (2022) to research using SM platforms.
2. Scope
REB review is required in all human research using SM platforms, with one exception – when participants have no reasonable expectation of privacy, and the information is in the public domain.
This document addresses if, and under which circumstances, REB review is required for research using SM platforms. Other pertinent ethical concerns associated with research using SM platforms (such as privacy, confidentiality, and consent) will be addressed in subsequent guidance documents. Given the evolving nature of digital research and SM platforms, this guidance and future guidance on the ethics of research using digital platforms are likely to evolve based on input from the community, technological developments, and changing practices in research disciplines.
As with the TCPS 2, this guidance is intended to apply to the broad spectrum of 'research' involving 'humans' as defined in the TCPS, and that fall within the scope of the policy (see TCPS 2 Interpretation, Scope #1, and Application of Article 2.1). This guidance is intended to be applied on a case-by-case basis within the specific context of research using SM platforms. It does not and cannot cover all types or methodologies of research or SM platforms. There will be exceptions or situations that are not covered and which should be guided by the core principles of the TCPS 2 (see Article 1.1) in consultation with the researcher's institutional REB.
In this guidance, references to specific types of SM platforms are intended for illustrative purposes only. SM platforms are of different types and serve different purposes and functionalities for their users. For example, Twitter allows profile owners to share information from their account in the form of short tweets. YouTube, another SM platform, allows account owners to upload videos with various levels of accessibility to the public globally. Some SM platforms, such as Facebook have built-in options that enable users to create personal profiles and share text, video, and photographs privately or publicly with their social network. Instagram and TikTok allow their users to create, watch, and share short videos. LinkedIn is an example of SM platforms that focus on professional identities, where profile owners share their employment history and personal information with their business network. Finally, digital platforms such as Airbnb, Yelp and Expedia may not be formally considered as SM platforms, but they include user content in the form of submitted reviews and recommendations.
Some SM platforms may be popular among certain communities that have shared characteristics e.g., rare diseases, shared conditions, or political views. Additionally, some SM platforms are often more popular among a specific age group. For example, Snapchat is an image messaging social platform typically used by youth and young adults, enabling them to chat with friends by using pictures that have a time-limited existence. The context and community served by the SM platform will inform an assessment of some of the risks inherent in the research being undertaken.
The focus of this guidance is not on the SM platforms themselves, but rather on the ethical considerations when proposing to use, or use information generated on, SM platforms for research purposes. Most SM platforms present similar ethical issues. The expectation is that much of the ethics guidance proposed in this document can also apply to other types of publicly utilized digital platforms, for example, information offered on websites, knowledge platforms (e.g., SharePoint), or service-oriented platforms that collect and publish user reviews (such as Airbnb or Yelp).
3. Information generated on SM platforms
Typically, individuals voluntarily generate information on SM platforms with an intent to share with their networks or followers. In general, most SM users do not specifically intend to create, share, or archive information on SM platforms for use as research data. Information on SM platforms can be about the individual holding the account/profile but may also include information about other individuals connected to the account holder. Most SM platforms allow users to create personal profiles and to upload information or multimedia for sharing with their social network privately, publicly or with certain limitations and conditions. Some accounts on SM are created by private individuals who may have an expectation of privacy, while others may be created by, or for, public figures to connect and share information in the public domain.
Information created by SM users is not typically generated as research data, but becomes research data when researchers collect, copy, or download it to apply a variety of research methodologies to analyze these data. This may be combined with other information, for example by using an application-programming interface. When their data are targeted for research, the users become prospective participants. When their data are used in research, they become participants.
Types of research using SM platforms
Research using SM platforms can be conducted in any discipline. It can be non-interactive, prospective, observational, or interactive, and each may involve varying levels of risk. Researchers may use existing information stored on SM platforms. Information collected using SM platforms for the purpose of research can be considered primary or secondary use of information. It may also include data linkage, which raises additional ethical concerns.
- Primary use of information: Information being collected prospectively from SM platform users for the purpose of research.
- Secondary use of information: Information created by SM platform users that is originally created for a purpose other than research, likely personal in this context - and that is now being used for research purposes (See Chapter 5, Section D).
Part II: Guidance
4. Does research using SM platforms require REB review?
Guidance in the TCPS 2 applies to research using SM platforms, regardless of whether it is primary or secondary use, akin to other contexts where researchers and participants are physically distanced and the use of remote or virtual means are required to communicate with participants. When used for research purposes, information collected using SM platforms, whether for primary or secondary use, falls within the TCPS 2 definition of human participants, which are "those individuals whose data, biological materials, or responses to interventions, stimuli or questions by the researcher, are relevant to answering the research question(s)" (Application of Article 2.1).
Research using SM platforms to collect new or use existing information is subject to REB review unless it meets one of the exemptions outlined in the TCPS 2. Chapter 2 of the Policy sets out possible exemptions from the requirement for REB review, where protections are available by means other than the REB. Articles 2.2 and 2.3 are particularly relevant in the present context.
Applicability of Article 2.2
Article 2.2 states:
Research does not require REB review when it relies exclusively on information that is:
- publicly available through a mechanism set out by legislation or regulation and that is protected by law; or
- in the public domain and the individuals to whom the information refers have no reasonable expectation of privacy.
The conditions set out in Article 2.2(a) for the exemption from REB review do not apply to research using SM platforms. While the information on SM platforms may be available to the public, it is not made accessible through a mechanism set out by legislation or regulation, and the information is not protected by a custodian/steward designated in accordance with legislation.
Article 2.2(b) stipulates two conditions that must be satisfied for the exemption to apply to research using SM platforms: (i) the information is in the public domain (discussed in detail in section 4a of this document), and (ii) the individuals to whom the information refers have no reasonable expectation of privacy (discussed in detail in section 4b of this document). For example, "REB review is not required for research that relies exclusively on cyber-material, such as documents, records, performances, online archival materials, or published third party interviews to which the public is given uncontrolled access on the Internet and for which there is no expectation of privacy" (Application of Article 2.2). Of note, while privacy may have been lost by the posting of stolen or otherwise unauthorized release of data, the original expectation of privacy remains and thus would not satisfy these criteria for exemption from REB review.
In principle, the TCPS 2 clarifies that where it is known that contributors of information to SM platforms have privacy expectations, research using such information must be submitted for REB review. This is the case, for example, "[w]hen accessing identifiable information in digital sites, such as online groups with restricted membership" (see Application of Article 2.2).
When in doubt about the requirement for REB review, researchers should consult their REB.
Applicability of Article 2.3
Article 2.3 states:
REB review is not required for research involving the observation of people in public places where:
- it does not involve any intervention staged by the researcher, or direct interaction with the individuals or groups;
- individuals or groups targeted for observation have no reasonable expectation of privacy; and
- any dissemination of research results does not allow identification of specific individuals.
Article 2.3 applies to "non-participant observational research" (also known as naturalistic observational research) that studies human acts or behaviours in a natural environment in which people partaking in their normal daily activities are observed with or without their knowledge by researchers who do not intervene in any way in the activity. This article applies where the researcher collects data through observation. For example, information collected from chats or by observing individuals' online activities and accounts/profiles that have been deemed to be accessible to the public (see section 4a of this document). A key consideration is determining what constitutes an observation within the context of research using SM platforms (see Chapter 10, Observational Studies).
The conditions (a) and (c) of Article 2.3 are elements within the researcher's control when planning for the research design, method, and dissemination plan. However, a key determinant for this exemption is whether the prospective participants have a reasonable expectation of privacy (see section 4b of this document).
When in doubt about the requirement for REB review, researchers should consult their REB.
4a. Is existing information on SM platforms considered "private", or "in the public domain"?
Existing information on SM platforms can be considered either private or in the public domain and drawing a line between the two may not be clear cut. For example, SM users will have registrations with personal data such as email and other demographic information, even if the content they generate on the SM platform is public.
Where the user account is registered as private, researchers will not typically have access to the information in the SM platform unless they seek the users'/prospective participants' consent.
If the information is accessible to the public, it may be considered in the public domain. However, there is a spectrum of access and other issues to consider when determining whether something is in the public domain for research purposes. Considerations may include the following:
-
Intent of users to make their information available to others
Before creating a profile, users of SM platforms must agree to the platform's terms of use. Users of SM platforms may be able to choose to adjust their privacy settings based on their preferences. In some cases, users may – or may not – have considered the full range of implications of their privacy settings and may or may not be fully aware of what information is, by default or by adjustment, available to others. Some SM platforms offer their account holders greater levels of control than others. For example, profile owners can manage their own privacy settings by keeping their account private or opting to make it (or some of it) available in the public domain. Some SM settings also allow users to control their audience, thereby actively deciding what they make public, and what content they share with contacts or a select group.
If existing information on SM platforms was created by its user with the intention that it would be available in the public domain with no restrictions, then such information can be considered accessible to others, including for research purposes. An example of information that exists in the public domain and can be freely available (i.e., no barriers at all) are comments on YouTube videos or opinions using hashtags where users intend to make their opinions known to others on specific topics. It may include videos posted by public figures e.g., politicians, influencers, athletes, or actors, with the intent to make the videos accessible to others in the public domain and with no expectation of privacy. In such cases, the information is intended to be accessible to the public without the need to get additional authorization, permission, or consent, and is likely to be exempt from REB review.
It is sometimes challenging to draw the line between private and public information. While this may not be the case for some users, this challenge likely results from several factors, and can be attributed to participants' vulnerability within the context of their participation in research. This includes, but is not limited to, a lack of awareness and capability because of age, cognitive impairment, or mental health challenges of users/prospective participants to draw the line between private and public information. Another factor to consider is the differing cultural perspectives on what is considered private versus public (see also section 4b of this document).
Where there is uncertainty about whether information is private or public, researchers may consider what a reasonable person would expect under the circumstance (discussed in detail in section 4b of this document). Where there remains uncertainty, researchers should consult their REB and should consider consulting the target community. When consulting their REB, researchers should provide relevant information and sufficient details to their REB to collaboratively make the determination of public versus private. If needed, REBs could consider having a standing member on the committee with this expertise, or bringing in an ad hoc advisor (as per Article 6.5) with the necessary expertise, or requiring the researchers to seek this advice.
-
Terms of use of the platform
Where the terms of use of the SM platform stipulate conditions that constitute restrictions for the generation, use, and distribution of information on the platform, this information may be accessible to the public but cannot be used for research purposes, unless the conditions of the SM platform's terms of use are met. Such conditions may include that researchers are required to formally request information from the platform administrator and are granted access in accordance with established criteria.
In response to user needs and concerns, administrators of some SM platforms have been modifying their settings from unrestricted or mostly unrestricted public access to more restrictive access, including additional protections. Examples include the limitations on data scraping for Instagram and Facebook. Researchers should therefore be cognizant that terms of use of SM platforms may evolve, and that they must follow the updated policies governing data and site security when using those sites.
-
Copyright/Intellectual property
In some cases, publicly accessible digital information may be accessible to the public but is subject to copyright, intellectual property rights or dissemination restrictions. This information is owned and protected by those controlling the information and must not be collected without their permission. Therefore, it would be required in these circumstances to obtain appropriately documented clearance from the legally authorized individual or entity before using the information for research purposes.
Researchers are expected to minimize privacy risks and develop data protection measures to de-identify the data, particularly where data linkage is involved. While this might not always be possible, researchers should minimize the risks to the community or group under study in their conduct of the research and dissemination of its results. This involves detecting identifiers that directly or indirectly point to an individual/community and ensuring that steps are taken to delete such identifiers, or de-identify or replace them with fake identifiers called pseudonyms or other de-identification codes. Researchers should be aware that the circumstances of individuals or groups may make them vulnerable in the context of research, and thus privacy and confidentiality concerns should be considered even for public information. Privacy legislation or regulations may apply and vary by jurisdiction (See Articles 5.1 – 5.3). Issues related to privacy and confidentiality in the conduct and review of research using SM platforms will be addressed in a future guidance document.
4b. Do participants have a reasonable expectation of privacy?
The TCPS 2 acknowledges that "[t]here are digital sites in the public domain where there is a reasonable expectation of privacy. Privacy expectations may be outlined in the sites' terms of use. When accessing identifiable information in digital sites of online groups with restricted membership, the privacy expectation of contributors to these sites is much higher. Research involving information from these types of sources shall be submitted for REB review (Article 10.3)" (Application of Article 2.2).
It is challenging to assess the reasonable expectation of privacy of individuals in general because it is a subjective assessment. This assessment is even more difficult when made online because it is difficult to verify the identity of the individuals.
The following are some considerations when assessing an individual's reasonable expectation of privacy:
-
The context of the research under consideration and its associated risks: REBs and researchers should consider the nature of the research topic, the research question, its design, methodology, and level of potential risk of harm to prospective participants. Risks should be assessed from a participant perspective, including risks related to reputation, employability, or financial standing, as well as embarrassment or even prosecution, if their information is disclosed.
-
The vulnerability of prospective participants within the context of the research: This includes considering the sensitivity of the collected information and examining the relationship between the circumstances of the individuals and groups that researchers aim to recruit and the proposed research question. SM posts may include sensitive information about criminal activity, financial problems, mental health issues, political views, or other potentially controversial topics or topics that may reveal or be subject to inferences. Targeted users, i.e., prospective participants, may create sensitive information about themselves or about others in text, photographs, or video posts - information that they may consider private in other contexts. For example, users may document their health condition to share with others who have the same condition, and this may reveal health information that would otherwise have been protected. Another example is that users may share information related to obtaining financial support with bad credit ratings, and that may reveal or imply their financial situation. REBs and researchers should be attentive to the possibility that vulnerability may be exacerbated by planned data linkage as part of the research design.
The vulnerability of individuals or groups can be further exacerbated by identification or re-identification within the context of the research. For example, where specific communities are the focus of the research, such as the case for Indigenous communities, the TCPS 2 advises that "[w]here the information can be identified as originating from a specific community or a segment of the Indigenous community at large, seeking culturally informed advice may assist in identifying risks and potential benefits for the source community" (Article 9.21). When relevant and appropriate, this guidance in Chapter 9 can apply to research using SM platforms targeting specific communities or groups, such as religious groups (Article 2.11).
On the other hand, users may create information in posts that include their views about preferences related to travel, food, exercise, or the weather. These are examples of information that many would consider to be less sensitive or unlikely to present risks if disclosed.
-
Researchers' knowledge of the prospective participant pool: It is necessary to consider the social, economic, and cultural contexts that shape the targeted users/prospective participants' life. Users may be legally acknowledged to have registered of their free will, and thus take on the risks/responsibilities of doing so. However, from an ethical perspective and based on their knowledge of the prospective participants' pool, researchers should consider the potential for participants' vulnerability within the context of the research. For example, users may post private content by sharing family photographs and personal memories in what is technically a public post, and not expect it to be subject to scrutiny by others. Something that is publicly accessible may be considered private in a prospective participant's culture (e.g., a religious or cultural group) or for a group of individuals with a specific medical condition.
Researchers should develop and demonstrate to their REB their strategies or mechanisms to familiarize themselves with the prospective participants' norms, practices, and privacy expectations, using a reasonable standard expectation. This serves to better assess privacy expectations from the participant perspective to the extent possible. An understanding of the prospective participant pool is even more important when the researchers do not share the same culture, language, or generation as the prospective participants. Questions to consider include:
- Do the characteristics of the participant pool suggest they are likely to have the capacity to understand that their posts can be viewed and used by others for other purposes, including research?
- Are they likely to be knowledgeable about their own privacy protections by managing the privacy settings of their SM profiles/accounts?
- Is there a risk of unnecessary inclusion or unjustified exclusion of populations in the research?
When in doubt or if unable to determine prospective participants' expectation of privacy (e.g., lack of information), researchers should consult their REBs.
4c. Summary
REB review is required in all human research using SM platforms, with one exception – when participants have no reasonable expectation of privacy, and the information is in the public domain.
To assess whether the exemptions in the TCPS 2 apply, REBs and researchers should consider the following two interrelated and overlapping factors: (i) whether the information on SM platforms is private or in the public domain, and (ii) whether the targeted users/prospective participants (i.e., the source of the information) are likely to have a reasonable expectation of privacy. The following illustration provides an overview of key factors to consider in determining the requirement for REB review of research using SM platforms.
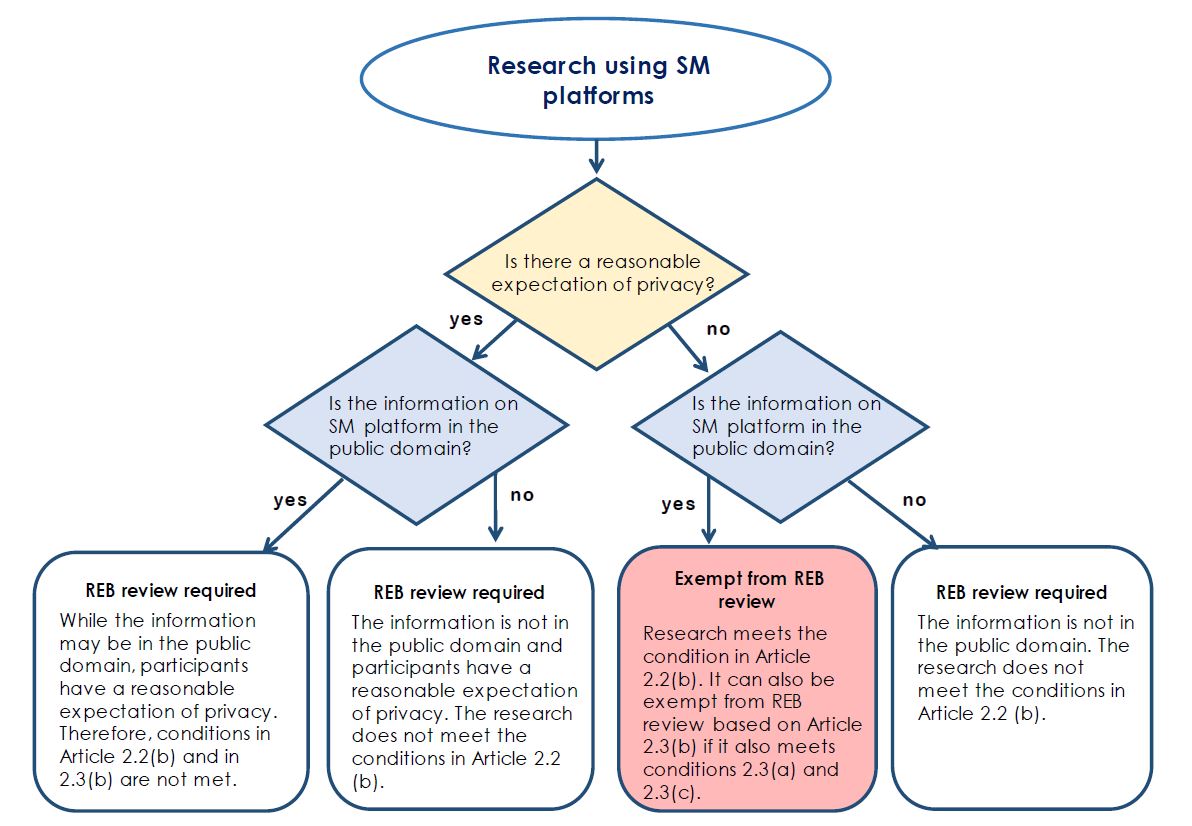
Long description
The flowchart summarizes key factors to consider in determining whether research using social media platforms requires REB review. To make this determination, there are two main questions:
-
Is there a reasonable expectation of privacy?
The answer to this question is either yes or no. Both lead to the second question.
-
Is the information on social media platforms in the public domain?
Similarly, the answer to this question is either yes or no.
The answers to both questions result in four outcomes, three of which state that REB review is required, and one that states that the research is exempt from REB review:
- First, if the response is yes to both questions, then REB review is required. In this scenario, while the information may be in the public domain, participants have a reasonable expectation of privacy. Therefore, conditions in Articles 2.2(b) and in 2.3(b) are not met.
- Second, if the response to the first question is yes, there is a reasonable expectation of privacy, and the response to the second question is no, the information is not in the public domain, then REB review is required. In this scenario, the information is not in the public domain and participants have a reasonable expectation of privacy. The research does not meet the conditions in Article 2.2 (b).
- Third, if the response to the first question is no, there is no reasonable expectation of privacy, and the response to the second question is yes, the information is in the public domain, then the research is exempt from REB review. In this scenario, the research meets the condition in Article 2.2(b). It can also be exempt from REB review based on Article 2.3(b), if it meets conditions 2.3(a) and 2.3(c). This is the only situation where research using social media platforms is exempt from REB review.
- Fourth, if the response to both questions is no, then REB review is required. In this scenario, the information is not in the public domain, so the research does not meet the condition in Article 2.2(b).
5. General ethical considerations and questions related to research using SM platforms
Where REB review is required, the onus is on the researchers to provide their REB with sufficient information to ensure an informed review of the ethical acceptability of the research using SM platforms (see Article 6.11).
When in doubt about the applicability of TCPS 2 or the requirement for REB review, researchers should consult their REB.
Where REB review is not required, researchers are expected to follow TCPS 2 and be guided by its core principles: Respect for Persons, Concern for Welfare, and Justice (see TCPS 2 Interpretation, Scope #10).
Where subject to TCPS 2, all guidance in the Policy applies. Each research project is different, and the nature of participant pools varies, so the considerations will vary on a case-by-case basis.
The following are some specific questions/issues that REBs and researchers should consider when determining the requirement for REB review, during the ethics review process, and in the conduct of research using SM platforms.
Knowledge of the SM platform
- When determining the requirement for REB review or to adequately conduct a review of the ethical acceptability of the research, does the REB have the necessary expertise or access to ad hoc advisors with knowledge and familiarity of SM platforms? An ad hoc advisor with expertise in digital media, social media analytics, cybersecurity, or computer science for example, can be consulted to provide up-to-date advice and knowledge to support such decisions. Where REBs expect to review research ethics applications that regularly require this expertise, they should appoint a member with the required expertise on the REB (see Article 6.5).
- Do the researchers demonstrate familiarity with the SM platform selected for use in data collection for their research? REBs may consider requesting confirmation from the researcher that they are complying with the terms of use of the SM platform.
Specific concerns and risks related to the selection of a SM platform for use in research
- Are the risks presented in the proposed research using SM platforms different from those related to in-person research?
- Are the potential risks for specific populations or communities altered with research being conducted on a SM platform?
- Does the intended use of the particular SM platforms within the context of the research suggest unique risks related to privacy and confidentiality, for example in the collection, transmission, and storage of digital information?
- Does the research involve data linkage? If so, what additional or new ethical concerns may be raised as a result of linking the data? For de-identified data sets, does linkage increase the possibility of potential re-identification?
- How does the intended use of the SM platform affect the risk/benefit ratio for participants? Are the use of the particular SM platform and information appropriate to answer the research question? Are there other preferable methods with lower risk or potentially greater benefit for participants?
Specific concerns/queries related to the participant pool
- How has the information been created on the selected SM platform?
- Is the information created by individuals and/or by another entity for the purpose of research – e.g. paid crowdsourcing to produce data (see TCPS 2 Interpretation, Fairness and Equity #4)?
- Is the information unauthorized for public release but available in the public domain. While this information may be in the public domain, proposed research with this data does require REB review. (See TCPS 2 Interpretation, Scope #16)?
- Is the information about, or created by public personalities who may not have privacy expectations? (See Article 3.6)
- Does the selected SM platform affect the representativeness of the participant sample or skew the inclusion/exclusion criteria?
- Are there unique risks to prospective participants in the consent process? Is there a need for alternative consent strategies?
- Is it likely that the information obtained using SM platforms may reveal more information than expected through visual images – e.g., photos that may include other individuals beyond the participants? How might this impact participants and those connected to them?
- Where the proposed research is based on community engagement or research agreements, how will the research integrate the use of SM platforms in the context of community engagement and research agreements? This is especially important in the conduct of research involving Indigenous communities (see Chapter 9).
- Are there other community constraints or institutional permissions required to begin recruitment or to continue participation in the research?
Special considerations
- Within the virtual context of conducting research using SM platforms, has consideration been given to developing strategies, where appropriate, for the management of incidental and material incidental findings including the discovery of situations that may trigger legal reporting obligations (e.g., suicidality or child neglect/abuse)? (See Article 3.4 and Guidance on how to address material incidental findings).
- While not a formal part of an REB's responsibilities, are there concerns about the safety of researchers working on sensitive or controversial topics and who may be subject to risks themselves? The REB should refer the researchers to other appropriate bodies within the institution to assess those risks. (See Chapter 2, Risks to researchers)
In addition to the TCPS 2, research using SM platforms should be carried out according to the professional standards of the discipline or field of research.
Part III: Practical Application
6. Scenarios
The following scenarios are intended to provide practical application of this guidance. They are examples that may not necessarily apply to the specific context of research under consideration.
When in doubt, researchers should consult with their REBs, and provide them with available details of the proposed research for REBs to assess the requirement for ethics review.
Some of the scenarios have been adapted from the publication, Social Media Research: A Guide to Ethics [ PDF (2.3 MB) - external link ], L Townsend, C Wallace - University of Aberdeen, 2016.
Scenario 1: Collecting information from closed forums
Context
A researcher wishes to study support mechanisms between members of a discussion forum which deals with mental health issues such as depression and feelings of suicide. This is a closed password protected forum, and registration must be approved by a gatekeeper (a site administrator).
Is REB review required?
This research requires REB review. It does not meet any of the conditions for exemption from REB review outlined in Articles 2.2 and 2.3 of the TCPS 2 because the SM platform is private, and from a participant perspective, the nature and topic of the discussions are likely to be sensitive (i.e., mental health issues surrounding depression and suicide). Therefore, users of this SM platform are likely to have a reasonable expectation of privacy.
Scenario 2: Research using information in the public domain
Context
A researcher wishes to study pro-legalization narratives on marijuana use. The information is publicly accessible on Twitter. The researcher will gather information over the last seven days posted with the hashtags #cannabis, #legalize and #ismokit.
Is REB review required?
In most cases, the research is likely to meet the exemption from REB review. Although the topic may be considered sensitive, information on Twitter is in the public domain, is accessible by anyone, including those without a Twitter account. Twitter users should not have an expectation of privacy given the nature of the platform. Exemption from REB review is based on the research meeting the conditions in Article 2.2(b). Also, it meets the condition in Article 2.3(b). It can be exempt from REB review based on Article 2.3, if the other two conditions 2.3(a) and 2.3(c) are satisfied.
Scenario 3: Research involving public figures
Context
A researcher wishes to explore the dominant themes in video posts by Olympic athletes on their social media profiles. The profiles are created as public and typically have hundreds of thousands of followers.
Is REB review required?
This research does not require REB review. The research meets the conditions for exemption from REB review outlined in:
- Article 2.2(b): The information created on the SM platform is publicly accessible. The profile users (Olympic athletes) expect others to view their information and what they post on SM, and any expectation of privacy would be unreasonable in such circumstances. Moreover, the nature of the information is not likely to be sensitive.
- Article 2.3: As there is no likely expectation of privacy, the condition in Article 2.3(b) is satisfied. Therefore, research exclusively collecting this information can also be exempt from REB review if it meets the other conditions in this article, 2(a) and (c): If there is no intervention by the researcher or direct interaction with the athletes, and while it may prove to be difficult or unnecessary to un-identify the athletes in the dissemination of the research, such dissemination must not allow identification of followers who post on the athletes' pages.
Scenario 4: Researcher with connection to participants
Context
A graduate student who is also a cancer survivor wishes to study cancer survivors' coping mechanisms following treatment. The student joins a Facebook page developed by a support group for breast cancer survivors where they share their experiences with treatment and how to manage challenges such as anxiety and depression during and after treatment. The contributors to this page appear to consider the platform a safe space to speak freely and to share resources with others who have similar experiences. The page includes identifiable information about the contributors who also share their own personal health information and identify others related to them.
Is REB review required?
This research requires REB review. It does not meet the conditions for exemption from REB review outlined in Articles 2.2(b) and 2.3(b) of the TCPS 2 given that participants are likely to have a reasonable expectation of privacy. While the student has access to the cancer survivors' Facebook page – including their personal information – the contributors have a reasonable expectation that those joining the group are respectful of their privacy.
Scenario 5: Research involving data linkage
Context
A researcher is interested in analyzing trends in political views and patterns across different social media platforms. The researcher collects information from Reddit, a SM platform that allows its users to post their views anonymously. The researcher plans to then compare those posts with other SM platforms by searching for other types of comments available online, analyzing patterns, and linking the data by writing styles.
Is REB review required?
This research requires REB review. Even though the information targeted for collection by the researcher is in the public domain with no reasonable expectation of privacy, researchers are required to submit their research for REB review when engaging in data linkage given the potential for identification. According to Article 5.7, "Researchers who propose to engage in data linkage shall obtain REB approval prior to carrying out the data linkage".
Scenario 6: Participatory research with potential for identifiability in dissemination
Context
A student wishes to study the prevalence of cyberbullying and its effects on high school students, using an online survey. The student will watch for trending Twitter hashtags relevant to the target participant pool and will post a link to a survey using hashtag questions such as views or experiences with bullying, as a way of soliciting comments and shaping the topic of conversation. In addition to the survey, the student will collect information from online cyberbullying support sites. The student will not collect identifiable information but plans to use quotes from both the Twitter comments and the cyberbullying support sites in a research paper and in conference presentations.
Is REB review required?
This research requires REB review. Even though the information targeted for collection by the researcher is in the public domain with an expectation that others will see this information, using quotes in disseminating the results of the research may identify the participants, and may further exacerbate participants' risk of stigmatization. The research does not meet the condition for exemption from REB review in Article 2.3(c). Posting a link to the survey to see the effect of the post on responses makes the research participatory involving researcher intervention. This is another reason that the research would not be exempt from REB review based on Article 2.3(a).
The researcher may also be at risk given the nature of the study, and while not the responsibility of the REB, consideration should be given to refer the student for institutional support, for example for risk assessment, or to ensure that their supervisor is highly involved to provide support.
- Date modified: